In the evolving landscape of application security, two terms have become increasingly prominent yet often confused: visibility and observability. While many security professionals use these terms interchangeably, they represent fundamentally different approaches to understanding and protecting applications. This distinction isn't merely semantic—it defines entirely different capabilities that can make or break your security posture.
The Iceberg Analogy: Surface vs. Depth
To understand the difference between visibility and observability, imagine an iceberg floating in the ocean. Visibility represents the small tip of the iceberg that breaks the surface—the part you can see from the outside. Observability, however, represents the massive underwater portion that contains the real substance and structure of the iceberg.
Visibility provides insight into the surface of events—the outcomes and consequences of what's happening in your applications. Observability gives you the ability to look inside the processes that bring those events to life in the first place.

The Limitations of Visibility-Only Approaches
While visibility has served the security industry well for decades, it comes with significant limitations that leave organizations vulnerable:
1. Surface-Level Analysis Only
Traditional visibility tools like Web Application Firewalls (WAFs) exemplify this limitation. WAFs claim to detect and protect APIs, but in reality, they only see the traffic generated by APIs—not the APIs themselves. They function as network sniffers, observing the outcomes of API calls without any ability to examine the underlying processes that created those calls. This surface-level view inevitably leads to:
- High rates of false positives
- Missed threats (false negatives)
- Insufficient protection for actual security needs
2. Outside-In Perspective
Dynamic Application Security Testing (DAST) tools demonstrate another visibility limitation. These tools launch simulated attacks against applications and watch for responses, drawing conclusions about vulnerabilities based solely on external observations. While useful, they cannot see inside the running application code or architecture, resulting in incomplete threat detection and numerous false alerts.
3. Inconclusive Analysis
Static Application Security Testing (SAST) tools highlight a third visibility constraint. They analyze application code for potential vulnerabilities but cannot observe the application in its running state. Without seeing how code actually executes in production, these tools cannot determine if identified code paths will ever be executed or exploited, leading to alert fatigue and missed real threats.
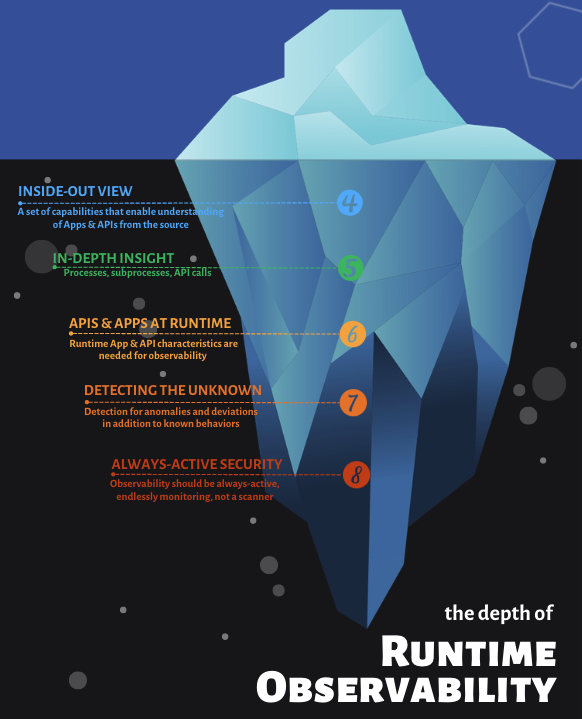
The Power of Runtime Observability
Observability addresses these limitations by providing insight into the processes themselves—not just their surface manifestations. True observability in application security offers several critical capabilities:
1. Inside-Out View
Observability enables you to understand applications and APIs from their source. Instead of guessing based on external traffic patterns, you can observe the running application code executing on the operating system, seeing exactly how APIs and application functions originate. This provides the most accurate foundation for analysis, vulnerability management, and protection against attacks.
2. In-Depth Process Insight
When application code is compiled, loaded onto an operating system, and executed, it becomes a process that spawns various sub-processes, including APIs. Observability provides deep insight into these sub-processes at the very moment of their origin, rather than trying to infer their behavior from downstream effects.
3. Runtime Analysis
True observability operates at runtime because that's when you can actually see code and architecture being executed. Rather than guessing about potential application behavior, you observe actual behavior as it happens. This real-time insight is crucial for accurate threat detection and response.
4. Detection of Unknown Threats
Perhaps most importantly, observability can detect unknown threats, including zero-day vulnerabilities. By monitoring the source of every process, API call, and code execution, observability systems can identify anomalies in application behavior—deviations from expected patterns that may indicate exploitation of unknown vulnerabilities.
5. Always-Active Security
Unlike intermittent scanning tools (SAST, DAST, SCA) that run periodically and then stop, observability provides continuous, always-active security monitoring. In today's threat landscape, leaving applications unprotected even for moments can be catastrophic. Observability ensures continuous protection throughout an application's entire lifecycle.
Building on Observability: Practical Applications
With true runtime observability, organizations can achieve capabilities that were previously impossible:
Complete Application Ecosystem Visibility
Observability enables you to see the entire application and API ecosystem in real-time. You can observe when Application A starts, when it makes an API call to Application B, when Application B queries a database, and so on. This provides a complete, accurate map of your application architecture as it actually functions.
Real-Time Asset Discovery
Instead of relying on documentation or architectural diagrams that may be outdated, observability continuously discovers and catalogs all APIs, visualizes call patterns, traces origins and destinations, and maps dependencies as they actually exist in production.
Accurate Vulnerability Detection
With complete visibility into running processes, observability enables the most accurate vulnerability detection and diagnosis possible, leading to more effective protection strategies based on actual rather than theoretical risks.
Lifecycle-Wide Coverage
While traditional tools work only on specific phases of the development lifecycle (SAST on the left side, WAF on the right side), observability works equally well across the entire DevOps lifecycle. The same capability and product can provide consistent security coverage from development through production.
.png)
The Complementary Relationship
It's crucial to understand that observability doesn't replace visibility—it complements it. Both capabilities are necessary for comprehensive application security. However, observability is at least as critical as visibility, and in many scenarios, even more important for protecting modern applications.
Key Takeaways for Security Leaders
- Recognize the Distinction: Visibility and observability are not just different words for the same concept—they represent fundamentally different security capabilities.
- Address the Gaps: If your security program relies solely on visibility tools, you're missing critical insights into the processes that create the events you're monitoring.
- Implement Runtime Observability: Complement your existing visibility tools with runtime observability to gain insight into application processes as they actually execute.
- Ensure Continuous Coverage: Move beyond intermittent scanning to always-active security monitoring that protects applications throughout their entire lifecycle.
- Build on Process Understanding: Use observability insights to create living, accurate architectural diagrams and asset inventories rather than relying on static documentation.
The distinction between visibility and observability represents more than a vocabulary evolution—it signals a fundamental shift in how we approach application security. While visibility has served us well by showing us the outcomes of application processes, the complexity and sophistication of modern threats require the deeper insight that only observability can provide.
By understanding and implementing both visibility and observability in your security program, you can move from reactive, surface-level monitoring to proactive, process-level protection. This shift is not just beneficial—it's becoming essential for organizations that want to stay ahead of increasingly sophisticated application-layer attacks.
The future of application security lies not just in seeing what happens, but in understanding why and how it happens. That understanding comes through the powerful lens of runtime observability.










