Application security isn’t new. Most enterprises already have some mix of SAST, DAST, and SCA in place—tools that have been around for decades and collectively represent a $5B market. Security teams have poured serious resources into buying tools, building AppSec programs, and scaling secure development practices.
But now that Runtime Application Security is on the rise, there’s a natural question: Does Runtime AppSec replace traditional AppSec—or can they actually work together?
Let’s break it down.
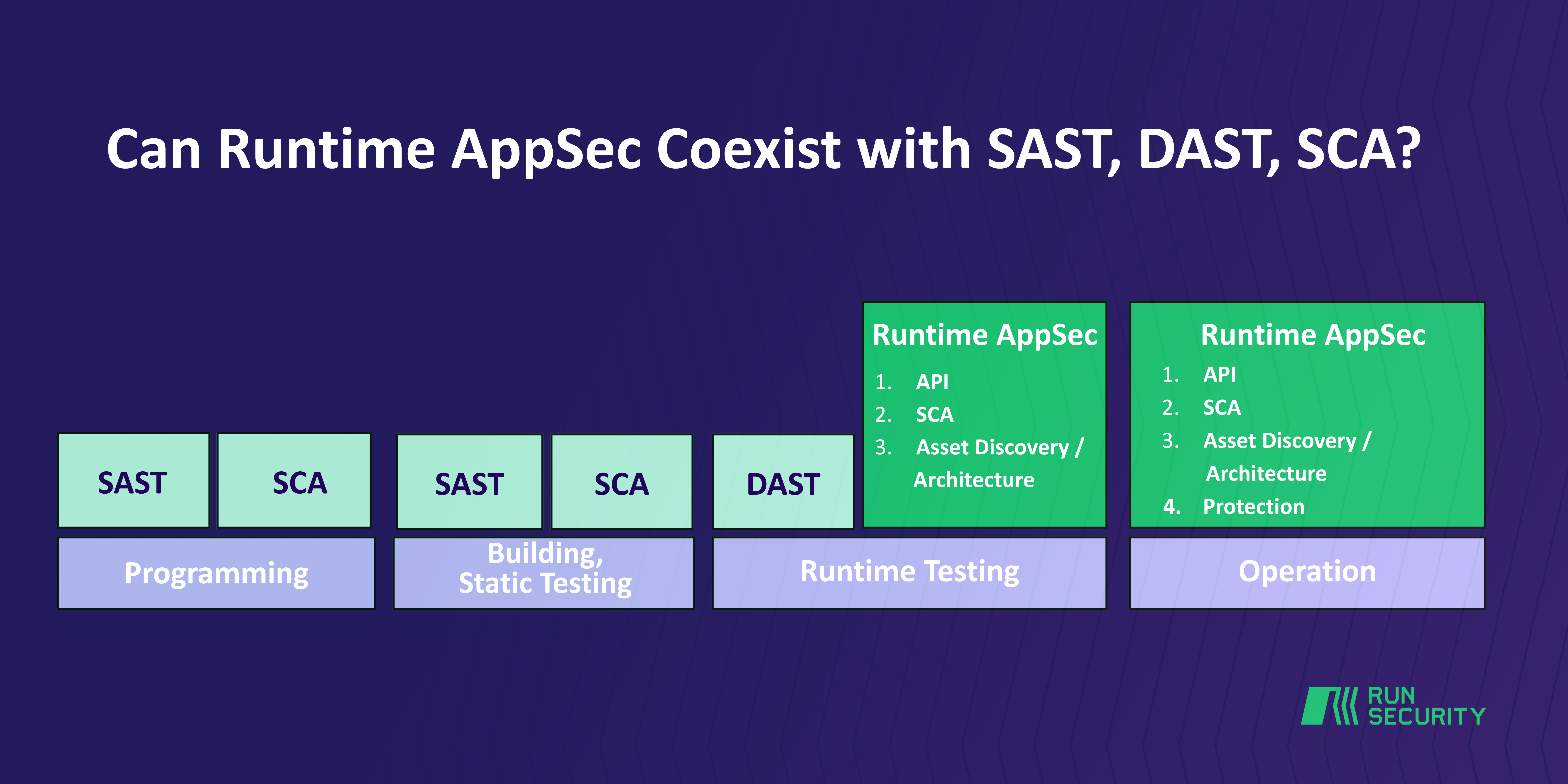
Where Traditional and Runtime AppSec Operate
SAST and SCA are static analysis tools. They work before runtime—during coding or static testing—long before an application is deployed. These tools catch issues early, making them great for shift-left security, but they stop short of showing what happens once the app is live.
Runtime Application Security doesn’t operate in these early phases at all. It only kicks in after the app is built and running, whether in a staging environment or full production. That means SAST/SCA and Runtime don’t compete—they complement each other.
➡️ TL;DR: No overlap, no conflict—just coverage across more of the application lifecycle.
Where Things Get Interesting: DAST vs. Runtime
DAST is the first traditional tool that operates during runtime testing, which is where it bumps into Runtime AppSec. But here’s the catch—Runtime goes a lot further.
✅ Better API security
✅ Runtime-level software composition analysis (SCA)
✅ Real-time service and asset discovery
✅ Dynamic architecture mapping of microservices, APIs, and OSS dependencies
DAST struggles with all of the above. Runtime doesn’t.
Production Is Where Runtime Shines
In production (the Ops phase), traditional tools mostly drop off:
- SAST and SCA? Not designed for live environments.
- DAST? Risky to use in production—it can trigger downtime.
- Runtime AppSec? Built for production. It thrives there.
Runtime AppSec not only detects threats and vulnerabilities in real time—it can also protect applications by blocking live attacks. Traditional AppSec was never designed for this kind of continuous, contextual defense.
The Verdict
Runtime AppSec and Traditional AppSec can and will coexist.
Enterprises can continue leveraging their existing investments in SAST, DAST, and SCA—especially early in the software development lifecycle. But to secure what's actually running, Runtime AppSec brings critical capabilities that traditional tools simply weren’t built to handle.










